Internal Strengths with External Opportunities
Internal Weaknesses relative to External Opportunities
Internal Strengths with External Threats
Internal Weaknesses relative to External Threats
In partnership with a SWOT analysis, the process of creating actionable intelligence (i.e. competitive intelligence) follows a number of stages with planning and initial data gathering. This process is cyclical and, therefore, the process requestor may generate further work after a product is finished. An example of the actionable intelligence cycle is outlined in Figure 3.0.
Figure 3.0 Actionable intelligence cycle
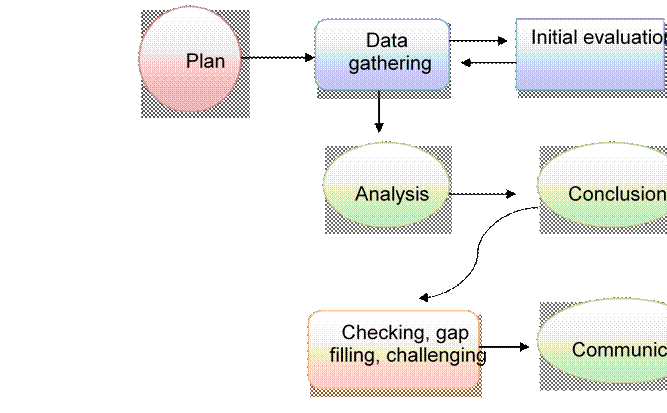
Source Murphy, 2005
The actionable intelligence cycle is defined by Murphy and is based on the US Central Intelligence Agency model (2005), which identifies five key elements in the above cycle.
1. Planning and direction: Decide on resources and intelligence strategies to apply.
2. Collection: How raw data is gathered and stored to form a knowledge base.
3. Processing: The unformed data retrieved is organised into a structured body of information.
4. Analysis: This category information will be used to manage the alerts, conclusions and recommendations based on the information obtained.
5. Dissemination: The findings will be presented to the end-users.
Bernhardt states that “wherever money is exchanged so is information” (1993) and there appears to be limitless access to this competitive information. McGonagle (cited in Trengrove and Vryenhoek, 1997, pg 26) provides an example list of sources and possible techniques which could assist with the ‘data gathering’ phase of competitive intelligence. This list has been detailed as Table 3.1.
Table 3.1Sources of Competitive Information
|
Sources of Competitive Information |
|
|
Government: agencies, departments, local government reports; Courts Patent and trademark applications; permit/planning applications
Specialised interests: academics and academic resources, publications, studies, research centres; Consumer and advocacy groups, product tests and comparisons, publications, studies. Experts, consultants, security analysis, expert witnesses. Trade associations, publications and membership directories, studies, meetings.
Private Sector: business information services, credit reports; Chambers of commerce. Competitors. Customers, suppliers, retailers and distributors of the target firm, advertising agencies, consultants, investment and commercial banks, agents, brokers.
Client employees: Sales/marketing/planning/engineering/purchasing, former employees of target firms. Target company; employees, catalogues and price lists, in-house publications, press releases and promotional materials, products, speeches, annual reports and other filings. Media: Business newspapers, magazines and wire services, advertisements, articles and reporters. Directories and reference aids. Local and national newspapers; advertisements, articles, reporters. Technical journals; articles and authors. Trade papers and journals; articles, advertisements, reporters, marketing studies. Financial periodicals. Security analysis reports. |
|
|
Techniques |
Explanation |
|
Obtaining information from recruits and competitor’s employees. Obtaining information from people who do business with competitors. Obtaining information from published material and public documents. Obtaining information by observing competitors and physical evidence. |
Job seekers eager to impress. Informal contact by specialists at conferences and trade shows. Key customers who are dealing with your competitors in different markets. For example, engineers on loan to a company. Analysing situations vacant advertisements. Department of Statistics information about an organisation. Buying competitors products. Benchmarking by analysing the best features of a competitor’s product. |
Уважаемый посетитель!
Чтобы распечатать файл, скачайте его (в формате Word).
Ссылка на скачивание - внизу страницы.