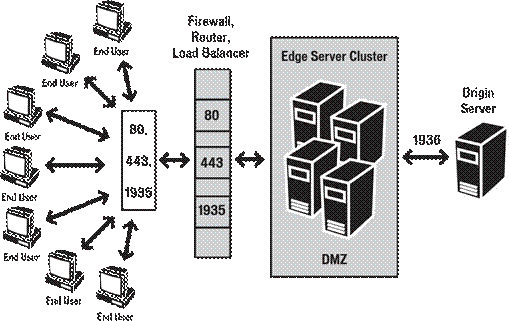
With the edge servers sitting in the DMZ, the network operators can open access to port 1936, avoiding the system overhead and risk of HTTP tunneling. Because the edge server performs stream splitting and stream caching, it uses the connection to the origin server efficiently, reducing the Internet bandwidth cost. The user also benefits from the more reliable connectivity.
Edge servers are defined by the values in the configuration files. Both explicit and implicit (also called anonymous) proxies intercept and aggregate the clients’ requests to connect to the applications running on an origin server. The explicit edge server prefixes its address to the origin server’s Uniform Resource Identifier (URI). This configuration makes the client (the user’s computer) aware of the proxy. The URI in the explicit proxy specifies the edge servers that will intercept the clients’ connection requests to the origin server.
The identity (the IP address and port number) of the implicit proxy is hidden from the client. The implicit proxy does not change or modify the routing information in the incoming URI before it connects the clients to the origin server. Edge servers are also defined as implicit proxies through the Flash proxy auto-detection process (FPAD).
Flash Media Server and network administrators can deploy Flash Media Server and route the incoming connection requests to the origin server through one or more edge servers. These implicit edges are transparent because the client is unaware of the proxy. They are also sometimes referred to as interception proxies. This deployment strategy is useful to ISP and telco providers for optimizing the flow of RTMP traffic through their networks.
Administrators can explicitly specify that any connection request to an origin server be automatically routed through an edge or proxy server. For example, if your applications are running on fms.foo.com, you can redirect the connection request from the users’ computers to another server (or virtual host) called fmsproxy.foo.com, which is configured to run in remote mode.
Instead of making the usual connection to the applications with the following connection string:
rtmp://fms.foo.com/app/inst
the clients are redirected through the edge, which prefixes its protocol and hostname to an existing URI: rtmp://fmsproxy.foo.com/?rtmp://fms.foo.com/app/inst
The prefix contains only the protocol, hostname, and optionally the port number. The URI must always end with a trailing slash. A question mark (?) separates the proxy’s prefix from the main URI.
Sometimes you cannot configure the client (as is the case with mobile phones and devices) to send their connection requests for Flash Media Server services through an edge or proxy server. In these cases you might set up one or more reverse proxy servers and position them closer to the origin server. Reverse proxies are usually located within an organization’s DMZ and control access to Flash Media Server resources from clients connecting through the Internet to an origin server located behind the firewall. Reverse proxies redirect incoming connection requests instead of outgoing connection requests as in the case of explicit and anonymous proxies.
The reverse proxy intercepts all connection requests that arrive from clients, as well as any edge servers positioned on the outer side of a firewall, authenticates these requests, and then forwards them to the origin server. The origin server is always located on the inner side of the firewall. With a reverse proxy, you limit the access to an origin server on the trusted network. The reverse proxy blocks all traffic except what its configuration allows for. A reverse proxy also blocks any attempt to access other servers and their resources on the trusted network.
Уважаемый посетитель!
Чтобы распечатать файл, скачайте его (в формате Word).
Ссылка на скачивание - внизу страницы.