However, the risk of competitive intelligence breaches increases (i.e. your competitors gaining access to your intelligence information) when the optimal level of knowledge sharing is exceeded. Figure 6.1 illustrates Rothberg and Erickson (2005) theory of optimal level of knowledge sharing.
Figure 6.1
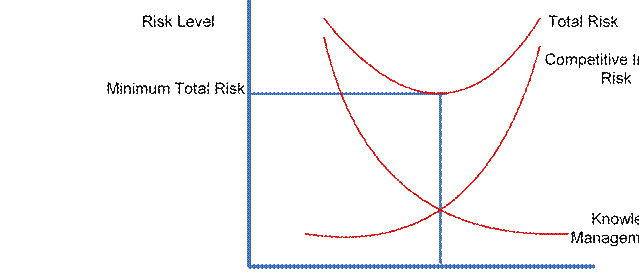
Knowledge SharingOptimal Level of Knowledge SharingAmount of
Furthermore, Rothberg and Erickson (2005) acknowledge that these knowledge assets must be protected and have developed a framework called the “Strategic Protection Factor (SPF)”, to assist with understanding and measuring the knowledge management and competitive intelligence risks. The framework includes four broad scenarios and includes the following descriptions:
SPF 5: Low KM Risk, Low CI Risk
Applies to industries like electrical products, insurance and air travel where there is little knowledge management and competitive intelligence risk. Generally knowledge is very individual and is difficult to share within the company or unintentionally with competitors.
SPF 15: High KM Risk, Low CI Risk
For organisations who have innovation but are typically not scientific or technological innovative. While operations, marketing and sales knowledge is important and needs to be shared, these organisations are better able to protect their knowledge assets as it is very specific to them. For example Microsoft, Coca-Cola and big accounting firms would fit this category.
Knowledge is shared widely across locations, people and functions and due to the nature of being particular, any knowledge gained by a competitor may ‘not fit within their environment’ because it is too specific, thus resulting in a lower competitive intelligence risk.
SPF 30: Low KM Risk, High CI Risk
Applies to organisations who find knowledge to be less critical to their success. While they may be innovative, their new products/processes are often too easily copied. Generally these organisations would range from auto and computer manufacturing to telecommunication service providers.
SPF 45: High KM Risk, High CI Risk
For organisations where developing and sharing knowledge is imperative for competitiveness and at the same time competitors are very interested in their proprietary knowledge.
Often these organisations have a strong Research and Development, advanced manufacturing and/or service operations which supply highly complex/technology products and solutions. An example of this industry would be pharmaceuticals where they are required to supply documented knowledge to the FDA for approval. Products are often protected and trademarked, but knowledge is not specific to the particular company. So knowledge is shared widely, resulting in a high knowledge management and competitive intelligence risk.
Now that we have an explored Rothberg and Erickson’s (2005) “Strategic Protection Factor (SPF)” to understand and measure the knowledge management and competitive intelligence risk, Marson’s (2006) key stages of the knowledge process for assessing and managing the risks of critical knowledge when leaving the organisation are now reviewed. This process has been displayed in Figure 6.2
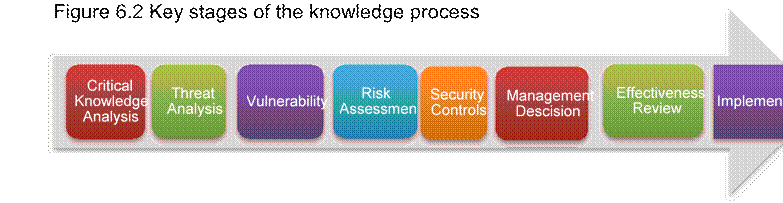
Critical knowledge analysis: The first stage includes identifying and reviewing the company’s critical knowledge, with the objective of understanding what knowledge might be targeted and its value.
Threat analysis: The next stage is to identify and review the threats which will assist with retaining the critical knowledge within the company. These threats could range from other competing companies, activists, pressure groups or even foreign government agencies.
Vulnerability analysis: The third stage identifies weaknesses in the company’s current capabilities in protecting their knowledge and information. This stage also includes the assessment or collection techniques that might be used, for example, legal and illegal, ethical and unethical.
Уважаемый посетитель!
Чтобы распечатать файл, скачайте его (в формате Word).
Ссылка на скачивание - внизу страницы.